Introduction
Cybersecurity is the practice of protecting the network, electronic systems, mobile devices, servers, computers, and data of the individual or organizations from various kinds of malicious attacks. Cyberattacks are one type of deliberate and malicious attempt by an organization or individual to steal information from another organization or individual. On 20th April 2020, ACSC published a paper namely ‘Threat update COVID-19 malicious cyber activity’. ACSC stands for Australian cybersecurity centre that targets to enhance cybersecurity all over Australia. During March 2020, the organization continues to receive various reports from government departments, businesses, and individuals about the COVID-19 related phishing campaigns, online fraud, and scams (Looi and Pring 2020). Therefore, the report will focus to identify and examine all types of malicious cyber activities identified and documented by the ACSC in this paper. The report will also demonstrate the identification and categorization of assets. Furthermore, five fundamental security principles of ACSC will be also analyzed in the report. Finally, the report will analyze the principle threat mitigation strategy proposed by the ACSC.
Discussion
All types of malicious activity identified by ACSC
In the ‘threat update COVID-19 malicious cyber activity’ paper Australian cyber security centre has been identified and documented various kinds of COVID-19 related scams. The main goal of this threat update named paper is to raise awareness about the evolving nature of COVID-19 themed malicious cybersecurity activities (Lallie et al. 2021). Therefore, all the malicious cyber activities identified by the ACSCS are provided in the below table:
| Name of the malicious cyber security activity | Details of the malicious cyber security activity |
|---|---|
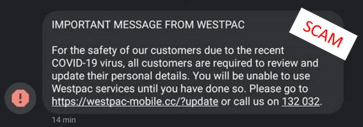
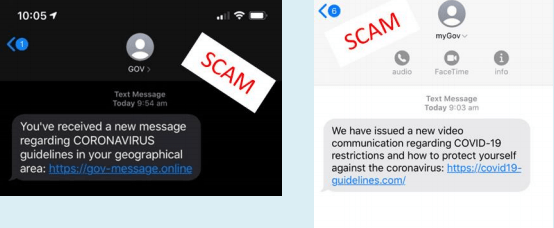
| Banking themed SMS phishing | On the date of March 30, 2020, the Australian cyber security centre has received almost 16 reports of banking themed SMS phishing. The cyber criminals send a Westpac themed phishing text which comprises a malicious link. The malicious link in the SMS directed the victims to a malicious website that attempts to steal credentials and personal information (Richter and Wilson 2020). The below figure shows the SMS that the cyber criminals utilized to steal the banking credentials of peoples.
|
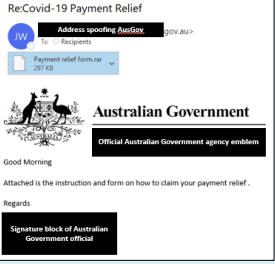
| Australian Government official spoofed in the email phishing campaign | On the date of 7th April 2020, the Australian cyber security centre received a report from one of the senior staff members of the Australian government department that was being spoofed. The Spoofing is a part of the COVID-19 themed phishing campaign (Khan, Brohi and Zaman 2020). The email comprises an attachment with implanted malware that was mainly created to steal important information like banking passwords and usernames. The below figure shows the email that is utilized to spoof:
|
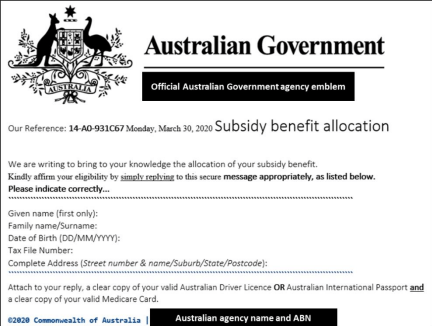
| Phishing campaign pretending to come from the Australian government | In March 2020, the peoples of Australia also have received some phishing emails that pretend to come from the Australian government. This specific Phishing email invites the people of Australia to provide their PII including the identity document (Medicare card, passport, and driving license) and tac file number to access the benefit in terms of money. The ACSC also identified that individuals who provide their personal information are prone to the risk of identity theft (Fayans et al. 2020). Through the utilization of this data, cyber criminals can take loans or cloud open bank account. The below figures shows the email:
|
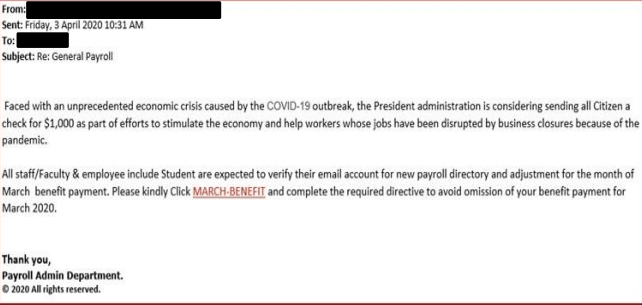
| Phishing email related to economic stimulus payment | On the date of 3rd April 2020, ACSC was received various reports that claiming, hundreds of employee of a large Australian organization has received a phishing email. The email asked the receiver to click on a link to receive a benefit payment of $1000. The link re-direct the users to a malicious website. The phishing email is shown in the below figure:
|
| COVID-19 testing related SMS phishing | On the date of 31st March 2020, the Australian government agency has reported the ACSC about a phishing SMS. The SMS has pretended to come from the government and requested the user to the malicious link. The below figure shows the SMS:
|
| Microsoft themed remote access scam | In March 2020, ACSC also identified another scam. In this scam, the scammer is impersonating a legitimate number of Microsoft and asked the victims to provide their date of birth and name for verification. After that, cybercriminals requested to download a remote access program that gives cybercriminals to access their computer. |
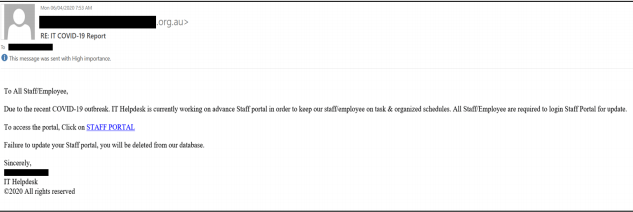
| IT helpdesk Scam | In March 2020, ACSC also identified a scam related to the IT helpdesk. In this scam, the cybercriminal sends a phishing email that pretends to come from the employer’s IT helpdesk. The email requested the staff to log into a new portal to get the latest task-related information. The screenshot of the email is provided below:
|
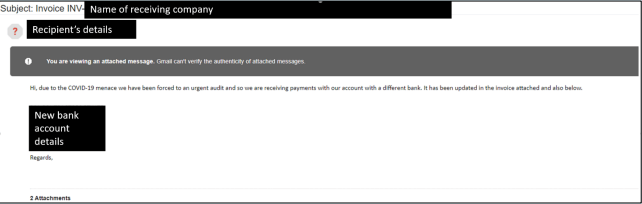
| Wire-Fraud Email | On the date of 26 March 2020, ACSC identified another COVID-19 themed wire-fraud email. The email provides bank account details and requested the user to transfer money to the new account. The phishing email is illustrated below:
|
Identification and categories assets
Asset identification describes the process in which some information can be used to identify the primary assets of the organization. Asset identification can also determine requirements for asset identification. Organizational assets can be categorized into few types such as tangible asset, intangible asset, current asset, fixed asset, operating asset, non-operating asset, and financial asset (Williams 2020). However, all types of assets are hold by the organization. In the case of any cyberattack, all the assets are impacted in the organization. Ownership, economic value, and resources are the main three aspects of the assets in an organization. In the given case study report, various types of attacks are identified have an impact on the assets of the organization. The primary type of assets is the people, procedure, data and information, software, hardware, and networking. Every organization needs to secure its assets through various safety measures and precautions. Human resources are the most essential asset of every organization. The success or failure of the organization depends on the assets directly or indirectly.
Peoples are the tangible asset in the organization as it has the physical existence in the organization. The economic value of the peoples in an organization is the highest. In the case of any cyberattacks, peoples are the primary target in the organization. However, the attackers can trigger an attack through the fault of the staff and the employees. Various procedures of the organizational operation are also targeted by the attackers (Offner et al. 2020). Any type of security gap can be the reason for the operational failure of the organization. These are the intangible assets of the organization as there is no physical existence in the system. Procedures are the combination of different factors in the system. The operational procedure, financial transaction, transport, product quality management are the most common type of procedures that can be attacked in an organization.
Data and information are some of the most essential factors that can be breached by the attackers. There are several data storages that contain sensitive data and information of the organization. Data storage should be protected by unique passwords and they must be kept in a secure locker. Data security should be considered by every organization for the operational integrity in the organization. Data and information security can be categorized as the intangible asset of the organization (Warren 2020). In the present world, the software is the primary asset of every organization as various types of tasks can be performed by the software. Software on the other hand performs a vital role in the performance of hardware in any system. The software can be categorized into the operating asset of the organization. Software plays a vital role in the operation of the entire system of an organization.
Hardware is another basic need of every organization which consists of different machines, infrastructure, workstations, and other equipment of the organizations. Hackers can influence the working method of the device through the software and procedures. However, the hardware of an organization can be categorized as the operational asset of the organization (Matas et al. 2020). In the case of any type of attack, hardware is the least affected element in any system. In order to secure the hardware devices for the attackers, different types of protective devices like firewall and VPN can be installed in the network of the organization.
On the other hand, the networking of the organization can be categorized as the operating asset. A secure network must be developed by the organization. Most of the security attacks can be performed by the attacker through the network gaps. The network is the primary media for the execution of the cyberattack. However, a secure network can also protect organizational integrity.
Identifying and prioritizing threats against each type of asset
In the above table, threats have been categorized on each of the assets of the organization based on the ACSC updated cyber activity. Justification has been given against each of the threats.
Five fundamental security principles with the security mitigation proposed by the ACSC
Security principles
Layering: In this type of security principle, several components are installed to protect the organizational activities (Gavra, Dobra and Pop 2020). However, each of the network components is provided with the backup security layer.
Limiting: In this security principle, access users are limited to the minimum permission to perform their work in the organization. Limiting access control attacking vectors on the data and information of the organization.
Diversity: It is closely related to layering as the breaching of one security layer does not compromise with the whole system security. By using a single technique, the attacker will not be able to break all the security measures.
Obscurity: This type of security principle is mainly used for the information security of an organization. It determines the security status inside an organization (Danenkov et al. 2020).
Simplicity: A secure system should be protected through a simple security layer. Sometimes, complex security measures become difficult to understand for the internal security experts of the organization.
Security mitigation technique proposed by the ACSC
In order to mitigate the security related issues, the Australian cyber security centre develops a mitigation strategy.
Mitigation techniques to prevent Malware delivery and execution are analyzed below:
- Application Control: The first mitigation technique proposed by the ACSC is application control that is very important to prevent the execution of malicious or unapproved programs including scripts, DLL, .exe (Muthuppalaniappan and Stevenson 2021). It is the fundamental security principle to prevent all non-approved applications from executing.
- Using Patch application: ACSC also recommended utilizing Patch in all applications including web browsers, Flash, PDF viewers, and Java. It is also important to utilize the latest version of all applications to protect the computer from extreme risks. Using a patch in the application is very much important because security vulnerabilities in the application can be utilized to execute the malevolent code in the system.
- User application: According to ACSC, web browsers needs to be configured in such a way that it can block Java, ads, and Flash on the internet. Configuring web browsers are important because Java, ads, and Flash is the popular way to execute malicious code on the system.
- Configure macro setting of Microsoft Office: It is another strategy proposed by the ACSC to block macros from the internet. This mitigation strategy is related to fundamental mitigation strategy as by configuring the Microsoft office settings, it is possible to mitigate block the cybercriminals to execute and deliver malicious code to the system.
Mitigation strategy to limit the cyber security incidents:
- Restricting administrative privileges: ACSC also recommended restricting the administrative privileges to applications and operating systems on the basis of user duties (Hakak et al. 2020). It is also important to don’t utilize privileged accountants for web browsing and email.
- Using multi-factor authentication: When Australian people perform privileged action, it is important to implement multi-factor authentication. Implementing multi-factor authentication is important to make it harder for cybercriminals to access systems and information.
- Patch operating systems: ACSC has proposed to patch all operating along with the application to mitigate extreme risks within 48 hours. It is also important for the Australian governments and Australian peoples to utilize the latest operating systems.
Mitigation strategy proposed by the ACSC to recover system information and data:
- Data backups: It is important for the Australian government to daily backups the important new or changed data. Large organizations of Australia need to test restoration initially, annually as well as when their information technology changes.
- Moreover, by following the above-discussed mitigation strategy, it is possible to mitigate all COVID-19 themed phishing schemes.
Summary
In this report, all the malicious security activities have been identified that are provided in the case study report. ACSC has received a large number of cybercrime report during the COVID-19 pandemic. All of the assets within an organization has been identified and the threats against each of the asset have been illustrated. However, a priority table has also been provided against different types of threats. Furthermore, the five fundamental security principles that are provided by ACSC have been demonstrated in this report. Moreover, all the Australian peoples, as well as the Australian government, need to follow the mitigation strategies of ACSC to mitigate all the COVID-19 themed phishing scams.
References
Danenkov, I., Kolesnikova, D., Babikov, A. and Iureva, R., 2020. Security by Design Development Methodology for File Hosting Case. In Smart Education and e-Learning 2020 (pp. 383-390). Springer, Singapore.
Fayans, I., Motro, Y., Rokach, L., Oren, Y. and Moran-Gilad, J., 2020. Cyber security threats in the microbial genomics era: implications for public health. Eurosurveillance, 25(6), p.1900574.
Feakin, T. and Weaver, J., 2020. An Australian perspective. Routledge Handbook of International Cybersecurity.
Gavra, V.D., Dobra, I.M. and Pop, O.A., 2020, May. A Survey on Threats and Security Solutions for IoT. In 2020 43rd International Spring Seminar on Electronics Technology (ISSE) (pp. 1-5). IEEE.
Hakak, S., Khan, W.Z., Imran, M., Choo, K.K.R. and Shoaib, M., 2020. Have you been a victim of COVID-19-related cyber incidents? Survey, taxonomy, and mitigation strategies. IEEE Access, 8, pp.124134-124144.
Khan, N.A., Brohi, S.N. and Zaman, N., 2020. Ten deadly cyber security threats amid COVID-19 pandemic.
Lallie, H.S., Shepherd, L.A., Nurse, J.R., Erola, A., Epiphaniou, G., Maple, C. and Bellekens, X., 2021. Cyber security in the age of covid-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Computers & Security, p.102248.
Looi, J.C. and Pring, W., 2020. Private metropolitan telepsychiatry in Australia during Covid-19: current practice and future developments. Australasian Psychiatry, 28(5), pp.508-510.
Matas, K., La, T., Grunchevski, N., Pham, K. and Koch, D., 2020, February. Invited tutorial: FPGA hardware security for datacenters and beyond. In Proceedings of the 2020 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays (pp. 11-20).
Muthuppalaniappan, M. and Stevenson, K., 2021. Healthcare cyber-attacks and the COVID-19 pandemic: an urgent threat to global health. International Journal for Quality in Health Care, 33(1), p.mzaa117.
Offner, K.L., Sitnikova, E., Joiner, K. and MacIntyre, C.R., 2020. Towards understanding cybersecurity capability in Australian healthcare organisations: a systematic review of recent trends, threats and mitigation. Intelligence and National Security, 35(4), pp.556-585.
Richter, A. and Wilson, T.C., 2020. Covid-19: implications for insurer risk management and the insurability of pandemic risk. The Geneva risk and insurance review, 45(2), pp.171-199.
Warren, M., 2020. 18th Australian Cyber Warfare Conference 2019 (CWAR 2019), October 7-8, 2019, Melbourne, Victoria, Australia.
Williams, A., 2020, March. Beyond 2000: The Rise of Australian Cyber Warfare Capability. In International Conference on Cyber Warfare and Security (pp. 549-XVIII). Academic Conferences International Limited.